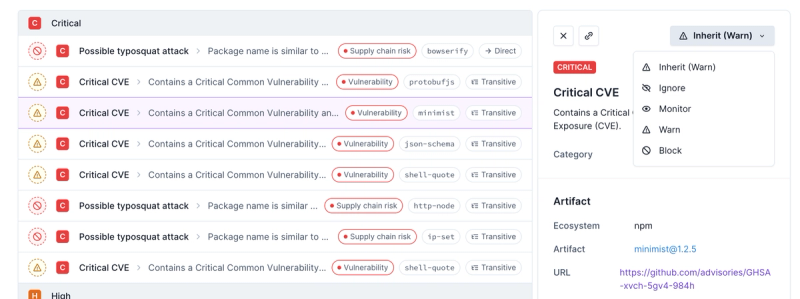
Product
Introducing Enhanced Alert Actions and Triage Functionality
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
@aws-cdk/aws-iam
Advanced tools
Changelog
0.9.2 (2018-09-20)
NOTICE: This release includes a framework-wide breaking change which changes the type of all the string resource attributes across the framework. Instead of using strong-types that extend cdk.Token (such as QueueArn, TopicName, etc), we now represent all these attributes as normal strings, and codify the tokens into the string (using the feature introduced in #168).
Furthermore, the cdk.Arn type has been removed. In order to format/parse ARNs, use the static methods on cdk.ArnUtils.
See motivation and discussion in #695.
addPartitionKey and addSortKey methods to be consistent across the board. (#720) (e6cc189)policy argument (#730) (a79190c), closes #672Readme
Define a role and add permissions to it. This will automatically create and attach an IAM policy to the role:
const role = new Role(this, 'MyRole', {
assumedBy: new ServicePrincipal('sns.amazonaws.com')
});
role.addPermission(new Permission('*', 'lambda:InvokeFunction'));
Define a policy and attach it to groups, users and roles. Note that it is possible to attach
the policy either by calling xxx.attachPolicy(policy) or policy.attachToXxx(xxx).
const user = new User(this, 'MyUser', { password: '1234' });
const group = new Group(this, 'MyGroup');
const policy = new Policy(this, 'MyPolicy');
policy.attachToUser(user);
group.attachPolicy(policy);
Managed policies can be attached using xxx.attachManagedPolicy(arn):
const group = new Group(this, 'MyGroup');
group.attachManagedPolicy('arn:aws:iam::aws:policy/AdministratorAccess');
FAQs
CDK routines for easily assigning correct and minimal IAM permissions
The npm package @aws-cdk/aws-iam receives a total of 121,241 weekly downloads. As such, @aws-cdk/aws-iam popularity was classified as popular.
We found that @aws-cdk/aws-iam demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 4 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
Security News
Polyfill.io has been serving malware for months via its CDN, after the project's open source maintainer sold the service to a company based in China.

Security News
OpenSSF is warning open source maintainers to stay vigilant against reputation farming on GitHub, where users artificially inflate their status by manipulating interactions on closed issues and PRs.